

Valencia pilot demonstration event
June 8, 2021
Valencia Pilot Demonstration Event
The demonstration event for the first Cyber-MAR pilot was conducted on 16 December 2020. The scenario defined for this pilot was based on the real electrical grid in the port of Valencia.
The architecture contains the part of the industrial network for providing power to all the systems, sensors, infrastructures, and companies in the port premises (blue box). It is composed of a fiber communication ring connecting six transformer stations distributed along the port. In addition, it contains all the systems and servers that a real port authority includes, such as firewalls, ERP, active directory, mail server, back-up servers, etc. Furthermore, it consists of the Cyber-MAR components deployed for the demonstration, which are described in the next section (light blue box). Finally, it has a system out of the port authority network, the MISP, used to synchronize known and new detected cyber-security incidents.
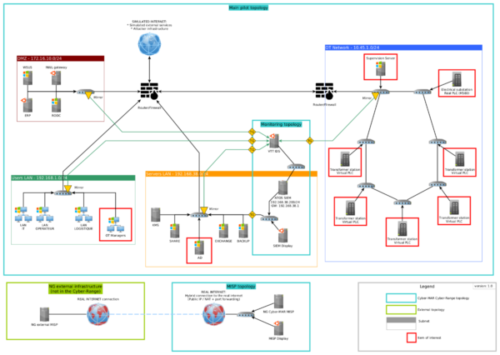
Figure 1 System architecture
The system infrastructure for the pilot relied on a Cyber-Range, where the topology was replicated for running any kind of cyber-attack. That allows critical operators to test the cyber-security of their infrastructure and train employees.
In the next figure the Valencia port authority network topology is depicted, which has been created for the pilot based on the aforementioned architecture.
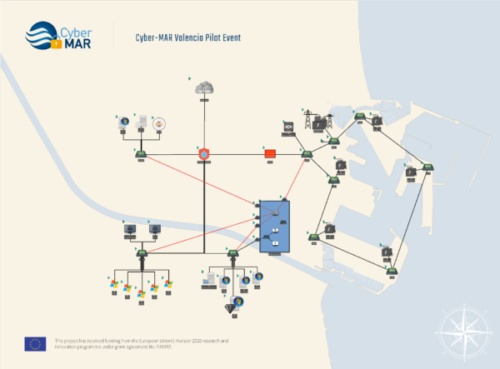
Figure 2 Valencia port authority network topology
During the demonstration, the OT port authority manager receives a SpearPhishing email from the attackers with an infected attached document. The initial infection vector is triggered, when they enable Macro content in the document: the malware is automatically executed.
Initially, the malware becomes persistent on the OT manager’s computer, and then it exploits the Zerologon vulnerability (CVE 2020-1472) to obtain administrator access on the Domain Controller (Active Directory). With this access, the malware can perform lateralisation through the network, infecting and installing persistently on the Active Directory server.
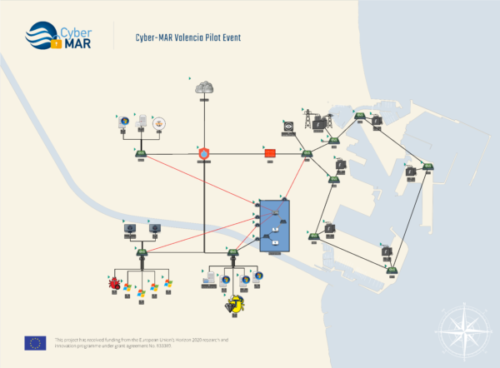
Figure 3 Valencia port authority network topology – infected
Once the malware infects this server, it can propagate to all the computers, systems and servers in the Domain immediately using the Windows Remote Management (WinRm), and setup permanent reinfection via the Group Policy Object. The malware also installs persistently on each infected system.
On each infected machine, the malware searches for SCADA management software, so it can start its main objective. The malware uses the Modbus protocol to access, stop and reprogram the real PLC with a compromised/broken program. This causes a power outage throughout the port.
A carefully crafted replacement program could also potentially cause physical damage to the power distribution infrastructure or downstream equipment.
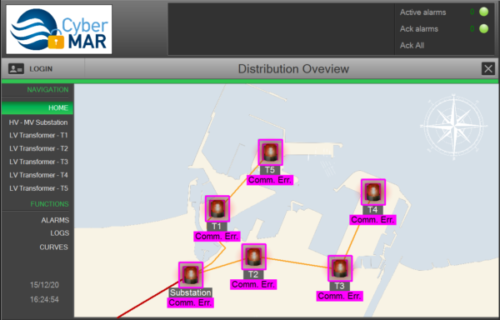
Figure 4 Infection propagated to all domain systems
Finally, each infected computer system, including the Active Directory, is encrypted with a Cryptolocking/Ransomware module, so the port users cannot access their files or systems without paying for the decryption key, or using (often incomplete) backups.
This also slows down restoration of the power distribution infrastructure.
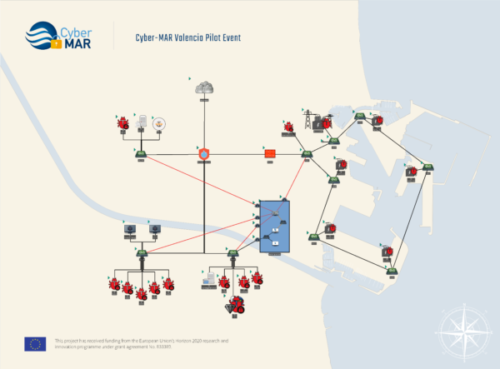
Figure 5 Cryptolocking/Ransomware encryption
During the event, the Cyber-MAR IDS and XL-SIEM components were detecting each of the steps of the attack and providing real-time information to the cyber-security team.
If you want to know more about this pilot demonstration event, you can find the recorded session below.

